In this blog post, we share our comprehensive WordPress Security Checklist, including our best practices for safeguarding a WordPress website from a wide range of potential threats, ensuring data protection, user trust, and site integrity.
As the world’s most popular content management system (CMS), WordPress is used by 45% of all websites on the internet in 2023. Due to its ease of use and flexibility to adjust to different website needs, it’s easy to see why WordPress is home to so many websites. But with millions of websites built on the CMS, its vulnerabilities have made it a frequent target for hackers looking to exploit security gaps.
From data breaches and website defacement to loss of user trust and SEO penalties, the consequences of a compromised WordPress site can be severe. This blog post dives into the complexities of WordPress security, how to prevent unwanted attacks and how to keep your site and the information of your users safe.
We’ve created the ultimate WordPress security checklist, whether you’re a blogger, business owner, or developer. Understanding and implementing WordPress security measures is not only wise but absolutely essential.
Why WordPress Security Matters
WordPress security matters significantly due to the potential consequences of a compromised site. When a WordPress website falls victim to cyber threats, the ramifications can be severe and far-reaching. It can result in the theft or exposure of sensitive user data, such as personal information, login credentials, and financial details, which can lead to identity theft and financial losses for users.
A compromised site can be defaced or injected with malicious content, damaging the website’s integrity and reputation. Search engines might penalize or blacklist the site due to malware or malicious activities, resulting in a severe loss of organic traffic and search engine rankings.
The loss of user trust is perhaps the most critical aspect of compromised WordPress security. Visitors to your site need to feel confident that their interactions are secure, and a breach of that trust can lead to a significant drop in user engagement, site traffic, and revenue. Ensuring WordPress security is not just about protecting the website but also about safeguarding the trust and confidence of its users.

Understanding Common Threats
Understanding common threats to WordPress sites is essential for strengthening your online presence. WordPress sites are vulnerable to various security risks, with some of the most prevalent threats including malware, hacking, and Distributed Denial of Service (DDoS) attacks.
- Malware, short for malicious software, can infiltrate your site through infected plugins, themes, or unverified downloads, and it can be used to steal data, insert harmful code, or even take control of the site.
- Hacking attempts often involve brute force attacks, where malicious users attempt to guess passwords, or exploiting vulnerabilities in outdated plugins and themes. Successful hacks can result in unauthorized access, defacement, or data breaches.
- DDoS attacks flood a website with an overwhelming amount of traffic, causing it to become unresponsive or crash, disrupting normal operations and potentially hiding other intrusion attempts.
- User Enumeration is a form of attack in which the attacker systematically scans a web application to uncover the login usernames associated with a WordPress-based site. It is a common technique employed by attackers to expose the usernames of WordPress sites.
These threats underscore the importance of keeping WordPress core, themes, and plugins up to date, using strong authentication, and employing security plugins to monitor and thwart potential attacks. Recognizing these threats and their methods of exploitation is the first step in safeguarding your WordPress website against them.
WordPress Security Checklist
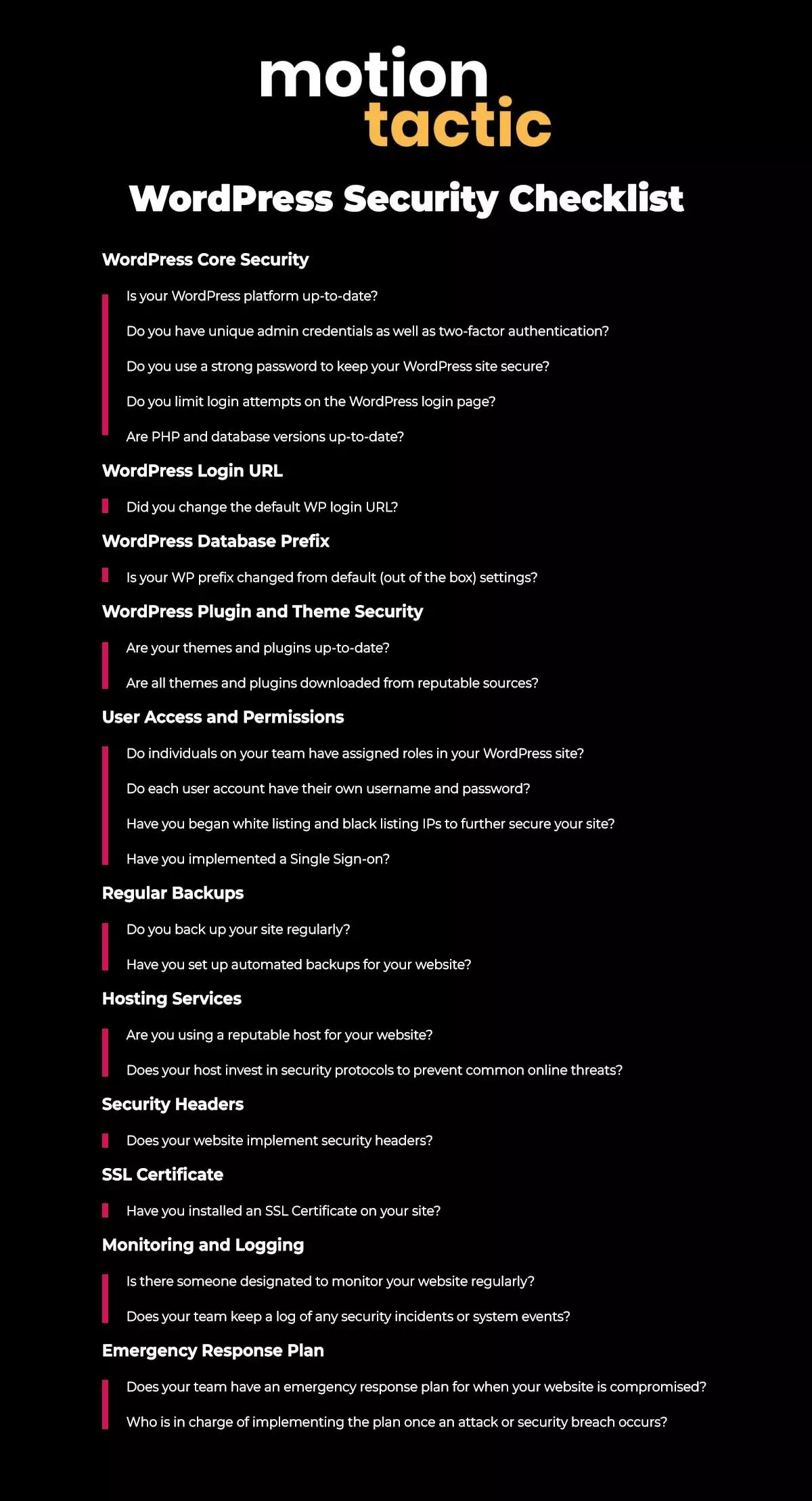
We’ve developed this WordPress Security Checklist to share our best practices for safeguarding a WordPress website from a wide range of potential threats, ensuring data protection, user trust, and site integrity. Each category below has questions to ask yourself or your web team to determine how safe your WordPress website truly is.
WordPress Core Security
- Is your WordPress platform up-to-date?
- Do you have unique admin credentials as well as two-factor authentication?
- Do you use a strong password to keep your WordPress site secure?
- Do you limit login attempts on the WordPress login page?
- Are PHP and database versions up-to-date?
WordPress Core Security is the foundation of a secure website, as it involves safeguarding the essential framework that powers your site. To secure your WordPress website, you must regularly update the platform. An up-to-date core also benefits from the latest security enhancements and bug fixes, making it more robust.
Additionally, using strong, unique administrator credentials and enabling two-factor authentication (2FA) provides an extra layer of defense. By paying attention to the security of the core software, you create a solid base on which to build a secure and trustworthy WordPress website, reducing the risk of unauthorized access and potential security breaches.
Staying up to date with PHP and database version updates is equally crucial. An outdated PHP version can expose your site to potential security risks, as older versions are more susceptible to known vulnerabilities. Updating your database version can provide performance improvements and security enhancements.
Neglecting these updates can leave your website vulnerable to attacks and compromise its integrity. By keeping all components up to date, you not only ensure the security of your WordPress site but also enjoy the benefits of enhanced performance and the latest features.
WordPress Login URL
- Did you change the default WP login URL?
The architecture of WordPress websites is widely known and open source, which means potential hackers have insights into how these sites function. For instance, the default WordPress login URL is typically structured as “www.example.com/login.php.”
This accessibility can make it simpler for potential hackers to initiate automated attacks. In many cases, when they can’t locate the login page, automated attacks are more likely to move on to other targets. By changing the default WordPress login URL, you can significantly reduce the susceptibility to potential attacks.
WordPress Database Prefix
- Is your WP prefix changed from default (out of the box) settings?
WordPress uses ‘wp_’ as the default table prefix in its database, which might not seem like a big deal, but it’s a security risk. This standard prefix can help hackers figure out your database structure, making it easier for them to breach your website’s security.
To boost your website’s safety, it’s strongly advised to change this default prefix. This simple action can go a long way in reducing the risk of unauthorized access and safeguarding your site’s data and features.
WordPress Plugin and Theme Security
- Are your themes and plugins up-to-date?
- Are all themes and plugins downloaded from reputable sources?
Plugin and theme security is a critical aspect to protect your WordPress site. The importance of regularly updating plugins and themes cannot be stressed enough. Developers release updates not only to introduce new features and improvements but also to patch known security vulnerabilities. Neglecting updates can leave your site exposed to potential exploits, making it a prime target for cyberattacks.
When updating, make sure you’re downloading plugins and themes from reputable sources. The WordPress Plugin and Theme Repositories are excellent places to find reliable, well-maintained options. By staying vigilant with updates and carefully selecting your plugins and themes, you’ll significantly reduce the risk of security breaches while maintaining the functionality and appearance of your WordPress site.
User Access and Permissions
- Do individuals on your team have assigned roles in your WordPress site?
- Do each user account have their own username and password?
- Have you began white listing and black listing IPs to further secure your site?
- Have you implemented a Single Sign-on?
User access and permissions in WordPress play a vital role in maintaining security and control over your site. The principle of least privilege is a fundamental concept, emphasizing that users should have the minimum permissions necessary to perform their tasks.
In WordPress, this translates into assigning specific user roles with corresponding permissions. By default, WordPress offers user roles such as Administrator, Editor, Author, Contributor, and Subscriber, each with varying levels of access. WordPress Admin have the most control, while Subscribers have the least.
To manage user roles and permissions effectively, it’s crucial to assign roles that align with the user’s responsibilities. For example, content creators should have Editor or Author roles, while site administrators retain the Administrator role. By adhering to the principle of least privilege and carefully configuring user roles, you can limit the potential damage and protect your website from accidental or malicious actions.
White / Black Listing IP address
Ensure that your IT team and trusted partners are whitelisted to prevent accidental blocking from accessing your site. Conversely, blacklist any individuals who are engaged in malicious activities. You can also configure your site to exclusively permit access from whitelisted IP addresses.
The product enables the seamless implementation of single sign-on, allowing integration with a company’s existing environment for a unified login experience on their WordPress site. This integration includes services such as Microsoft 365, Salesforce, and Okta.
Regular Backups
- Do you back up your site regularly?
- Have you set up automated backups for your website?
The importance of backing up your WordPress site cannot be overstated. It serves as a safety net, ensuring that even if your site experiences a catastrophic failure, a cyberattack, or an accidental data loss, you can quickly restore it to a previous state.
To set up automated backups, you can utilize reliable backup plugins like UpdraftPlus or Jetpack, which offer easy-to-configure options to schedule regular backups. It’s essential to choose a backup frequency that aligns with your content update schedule, but daily or weekly backups are typical choices. Many hosts also offer automated backups, which will save you from needing an additional plugin to back your website up for you.
Additionally, store backup files in secure, offsite locations, such as cloud storage services like Google Drive or Dropbox. Automated backups provide peace of mind and save you from the potential nightmare of data loss or website downtime, making them a crucial component of a robust WordPress security strategy.
Hosting Services
- Are you using a reputable host for your website?
- Does your host invest in security protocols to prevent common online threats?
Choosing a secure WordPress hosting provider is of paramount importance when it comes to ensuring WordPress website security. Your hosting environment is the foundation on which your website operates, and its security measures can significantly impact your site’s vulnerability to threats.
A reputable hosting provider typically offers security features such as firewalls, intrusion detection systems, regular server software updates, and data backups, all of which play a critical role in safeguarding your website.
They also invest in robust security protocols to protect against Distributed Denial of Service (DDoS) attacks, malware, and other common online threats. A well-chosen hosting provider not only reduces the risk of security breaches but also ensures that your site remains accessible, responsive, and reliable, thereby contributing to a positive user experience and enhancing your website’s overall security posture.
Our recommended hosting providers:
Security Headers
- Does your website implement security headers?
Security headers are a crucial component of WordPress website security. These headers are HTTP response headers that provide additional layers of protection to your website by instructing browsers on how to handle certain aspects of web security.
For instance, HTTP headers like Content Security Policy (CSP), X-Content-Type-Options, and X-Frame-Options can help protect your site against various threats such as cross-site scripting (XSS) attacks and clickjacking.
By implementing security headers, you can control how your site’s resources are loaded and interacted with, preventing unauthorized content from being loaded or executed in the browser. Properly configured security headers ensure that your site complies with best security practices, reducing the risk of common web vulnerabilities and enhancing the overall security of your WordPress site.
For more tips on adding the following code to your website, visit this WP Engine page or this Pantheon guide.
SSL Certificate
- Have you installed an SSL Certificate on your site?
SSL (Secure Sockets Layer) certificates are primarily responsible for encrypting the data transmitted between a user’s browser and the web server. This encryption ensures that the information exchanged, such as login credentials, personal details, and payment information, remains confidential and secure during transit.
SSL certificates establish a secure, encrypted connection, denoted by the HTTPS protocol, which protects against eavesdropping and man-in-the-middle attacks. They are essential for data privacy and the protection of sensitive information, especially for websites that handle user data and online transactions.
Installing an SSL certificate on a WordPress website involves a few steps. Here’s a general guide on how to do it:
- Obtain an SSL Certificate
- Check Your Hosting Environment: Ensure that your web hosting environment supports SSL certificates. Most hosting providers support SSL these days.
- Install the SSL Certificate: The installation process may vary depending on your hosting provider.
- Update Your WordPress Website Settings: After installing the SSL certificate, you should update your WordPress site settings to use HTTPS instead of HTTP.
- Redirect HTTP to HTTPS: To ensure all traffic goes through the secure HTTPS connection, you should set up a redirect from HTTP to HTTPS. You can do this using a plugin or by editing your .htaccess file if your hosting environment allows it.
- Test Your SSL Installation: Visit your website with “https://” to confirm that the SSL certificate is installed correctly and the padlock icon appears in the browser’s address bar.
- Update Links and Content: After enabling SSL, ensure that all internal and external links within your site use “https://” instead of “http://” to avoid mixed content issues.
- Set Up an SSL Certificate Renewal Reminder: SSL certificates typically have an expiration date. Set up a reminder to renew the certificate before it expires to ensure uninterrupted security.
- Keep in mind that the specific steps may vary depending on your hosting provider and the SSL certificate type you’ve obtained. If you’re unsure about any part of the process, consult your hosting provider’s documentation or customer support for guidance.
Monitoring and Logging
- Is there someone designated to monitor your website regularly?
- Does your team keep a log of any security incidents or system events?
Continuous monitoring helps in the early detection of suspicious activities and potential security breaches. It enables you to identify and respond to threats in real-time, thereby minimizing damage and loss. Maintaining detailed logs is valuable for post-incident security analysis.
Logs record critical information about user interactions, system events, and potential security incidents. They serve as a historical record of what transpired on your site and are crucial for investigating and understanding security incidents, as well as for compliance and legal purposes.
By proactively monitoring your site and diligently maintaining logs, you can effectively bolster your security, promptly address any irregularities, and better protect your WordPress site from potential threats.
Emergency Response Plan
- Does your team have an emergency response plan for when your website is compromised?
- Who is in charge of implementing the plan once an attack or security breach occurs?
Having a plan for if / when your website is compromised is a crucial element of any security strategy. It serves as a blueprint for handling security breaches and minimizing damage in the event of an incident. The need for such a plan is clear, as timely and effective action can make the difference between a minor issue and a major security crisis.
- The first step is to identify and acknowledge the breach, then isolate and contain it to prevent further damage. This can involve temporarily taking your site offline or limiting access.
- Next, you should notify stakeholders, including team members, hosting provider, and possibly law enforcement if sensitive user data is involved. Simultaneously, start an investigation to understand the extent of the breach and how it occurred.
- Once the breach is contained, remove the malware or compromised code and, if necessary, restore your site from a clean backup.
- After resolving the issue, implement enhanced security measures to prevent future breaches.
Having a plan helps maintain your site’s integrity, user trust, and reputation by enabling a swift and coordinated response to security incidents.
Final Thoughts
Safeguarding your WordPress site is not just an option—it’s an absolute necessity. This comprehensive WordPress Security Checklist has guided you through the critical aspects of protecting your site against the myriad of potential threats it may encounter.
From core security updates to user access management, backups, and the crucial role of your hosting provider, we hope this post has equipped you with the knowledge and tools to create a robust security strategy.
By understanding the common threats faced by WordPress websites and staying proactive to secure your website, you’ve taken a significant step toward maintaining data protection, user trust, and the overall integrity of your online presence.
The importance of securing your WordPress site cannot be understated, and with this checklist as your guide, you’re well-prepared to navigate the complex realm of web security, making your website a safer and more resilient place for both you and your users.
Additional Resources
WordPress Security Plugins
The impact of security plugins on website performance can vary depending on the specific plugin and how it’s configured. Some security plugins can potentially add overhead to your website, but it’s important to compare them in order to find a plugin that is right for your website.
Here are some factors to consider:
- Plugin Quality: Well-coded security plugins are designed to have a minimal impact on site performance. They are optimized for efficiency.
- Configuration: Properly configuring your security plugin is essential. Some features may impact performance more than others, so you should enable only what you need.
- Caching: Combining a security plugin with a caching plugin can help mitigate any performance impact by reducing the need to run security checks on every request.
- Server Resources: The impact on website performance can also depend on the server resources available. On a powerful server, the impact may be negligible, while on a shared hosting plan with limited resources, it might be more noticeable.
- Regular Updates: Ensure that the security plugin you choose is regularly updated. Updates often include optimizations and bug fixes that can improve performance.
Here are a few security plugins we recommend:
In summary, using a security plugin is generally a good practice for protecting your WordPress website. While there might be a small performance impact, it’s usually a worthwhile trade-off for the added security and peace of mind. Just be mindful of your specific requirements, choose a reputable security plugin, and optimize its configuration to suit your needs and server capabilities.
Feel free to share our WordPress Security Checklist below!